Read by Security Assistant
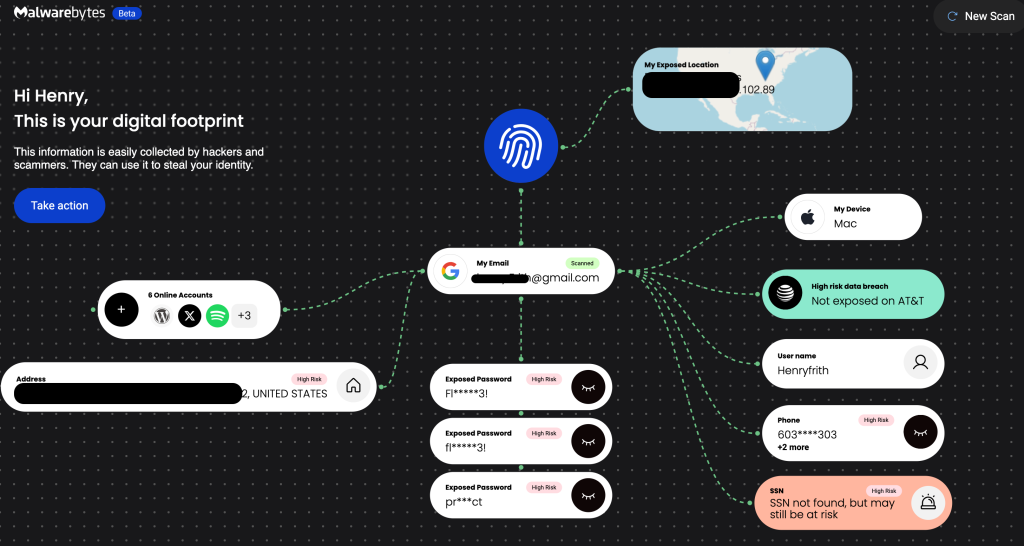
I wrote a blog post back in April when the breach was first discovered. We now have additional information on what was taken. At the bottom of the post, I share a link where you can check if you were exposed in this breach or other breaches. You can see some of my digital footprint that is on the dark we.
A Brief History of AT&T Breaches
AT&T, one of the largest telecommunications companies in the United States, has faced several data breaches over the years. These incidents have exposed the personal information of millions of customers, making them potential targets for cybercriminals. In the most recent breach, personal data such as Social Security numbers, birthdates, contact information, and even phone records were compromised, although certain critical data remained secure.
What Was Stolen in the Latest Breach?
In the latest breach, the following types of data were stolen:
- Customer Names: Full names of account holders.
- Contact Numbers: Phone numbers linked to the accounts.
- Physical Addresses: Home addresses provided for billing and service purposes.
- Social Security Numbers: Unique identifiers used for identification and credit checks.
- Date of Birth: Personal identifiers critical for various verification processes.
- Phone Records: Call logs, including numbers called, duration, and time of calls.
- Text Messages: Contents and metadata of text messages sent and received.
What Data Was Not Available in the Most Recent Breach?
It’s important to note that some highly sensitive information was not compromised in the latest breach. This includes:
- Credit Card Information: Payment card details were not accessed.
- Bank Account Details: Banking information remained secure.
- Passwords and PINs: Login credentials and PINs were not leaked.
While this might provide some relief, the data that was stolen can still be used in various malicious ways.
How Threat Actors Can Use the Stolen Data
Threat actors can use the data from the AT&T breach in multiple ways to harm individuals. Here’s how they might combine this data with information from other breaches to target you:
- Exploiting Phone and Text Records:
Access to your phone and text records can be particularly invasive. Attackers can identify patterns, personal contacts, and sensitive conversations, which can be used for blackmail, further phishing attacks, or to gather more intelligence on you.
Protecting Yourself
To protect yourself from the potential fallout of the AT&T breach, consider the following steps:
- Monitor Your Accounts: Regularly check your bank and credit accounts for any suspicious activity.
- Enable Two-Factor Authentication (2FA): Use 2FA on all accounts that offer it to add an extra layer of security.
- Be Skeptical of Unexpected Contacts: Be wary of unsolicited emails, texts, or calls asking for personal information.
- Use Strong, Unique Passwords: Ensure your passwords are strong and unique for each account, and consider using a password manager.
- Check Your Credit Reports: Regularly review your credit reports for any unauthorized activity.
By understanding the risks and taking proactive measures, you can better protect yourself against the misuse of your personal information.
The screenshot shows the information that is available to the threat actors on my personal email account. You can check your email address using the following link. This is a free service from Malwarebytes that is still in beta, but it will give you an idea on what info about your account the threat actors are using.
Digital Footprint Portal | Malwarebytes